Airwall
Purpose built to secure critical infrastructure using an identity based, zero trust protocol.
Airwall product summary
- A complete zero trust portfolio.
- Securely connect anything, anywhere over any network.
- Private overlway networks on top of existing infrastructure, no need to rip and replace.
- Easy to manage identity-driven policies.
- Micro-segmentation with end-to-end encryption.
- Reduces attack surface by 95% while reducing cost and complexity by 50-80%.
How does it work?
- Creates private overlay networks based on encrypted tunnels and trusted cryptographic identities to secure network traffic.
- Airwall provides total control over communications.
- Single pane of glass management console provides simple, scalable, and extensible policy management between things.
- Based on Host Identity Protocol (HIP), an open IETF standard developed to fix the lack of mobility and security flaws of TCP/IP.
Highly available and resilient to network changes. Nothing behind an Airwall has ever been hacked.
End-to-end encryption
HIP tunnels ensure secure traffic between devices, no intercepted traffic over a global network. Set up your private overlay network independent of network perimeters.
Learn MoreIdentity-based policies
Easily align security policies with identity of users and devices. Authorization restricted to cryptographic ID and multi-factor authentication.
OT visiblity
Combine secure communication and policy enforcement with traffic visibility, correlation and threat detection with our ability to mirror traffic to third-party threat detection solutions.
Learn MoreSoftware-defined orchestration
Simplify management and orchestration of security policies, protected devices, authorized users and groups and globally managed private networks through centralized software-defined controller.
Connect anything-anywhere securely
Easy to deploy over any IP network for remote access and cloud applications. Avoid fork-lift upgrades and vendor architecture lock-in.
Airwall works with any network infrastructure.
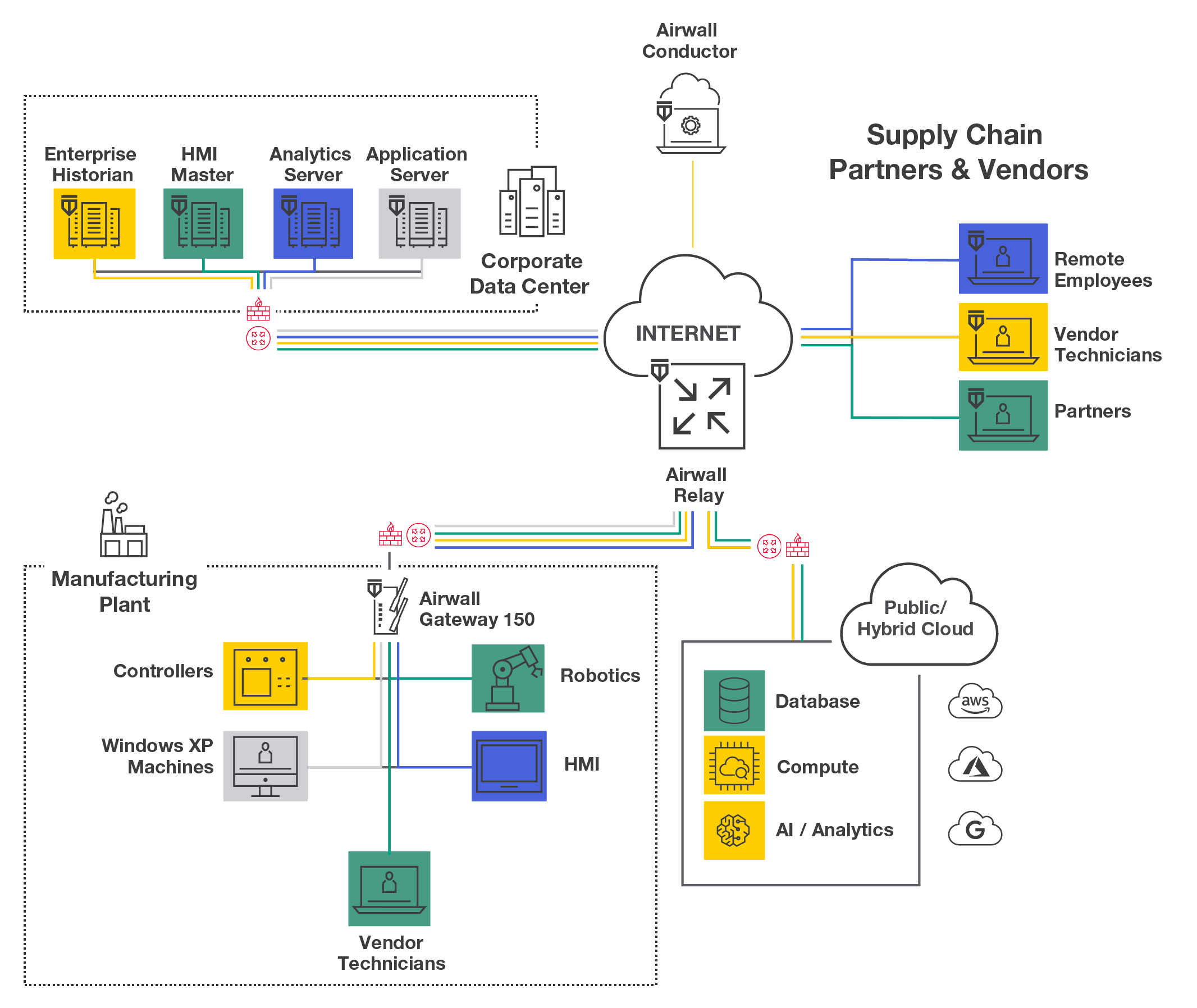
Airwall provides a completely private overlay network on top of shared, public, or even compromised infrastructure, that is both more secure and quickly and easily managed. It can deploy and operate at a fraction of the cost of other more complicated piece meal approaches, like firewalls, VPNs, VLANs and ACLs.
The network you want
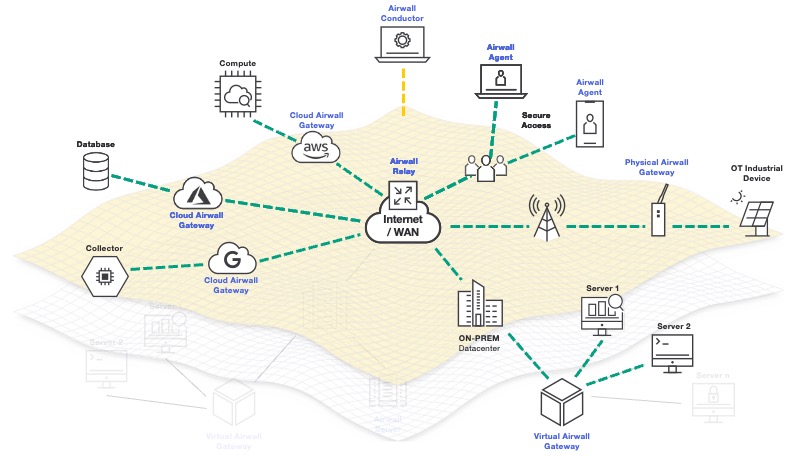
Built on a secure foundation.
Airwall uses the more modern Host Identity Protocol (HIP) to implement a zero trust model before connections are even established. This IETF standard natively encrypts, microsegments, and securely connects, reducing your attack surface, eliminating unauthorized access, lateral movement, and malware propagation.
Simple segmentation