Deploy Airwalls
across on-premise, remote, virtual or cloud environments.

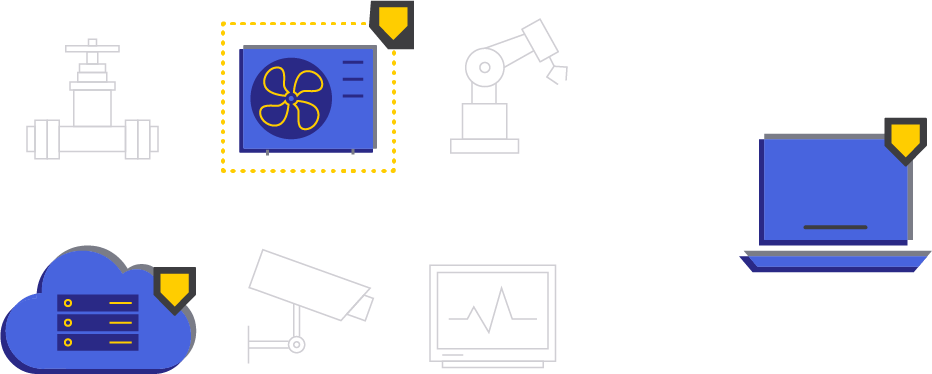
Connect anything, anywhere with end-to-end encryption and MFA.

Make critical assets and infrastructure impervious to threats.

Because identity is not tied to location, when an asset moves, policy follows.

Remove complexity by simplifying creation and enforcement of policies.
Protect critical infrastructure from discovery & attack.
Manage employees, vendors, third parties.
Secure data transport from critical infrastructure to cloud, and back.
across on-premise, remote, virtual or cloud environments.
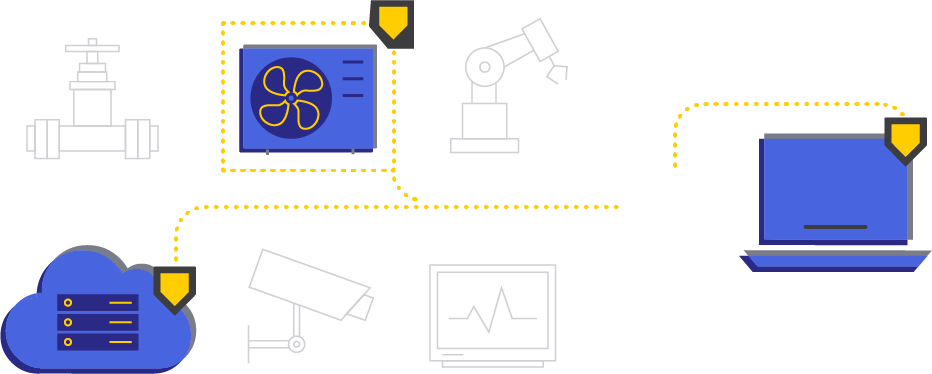
based on identity and explicit permissions according to zero trust principles.
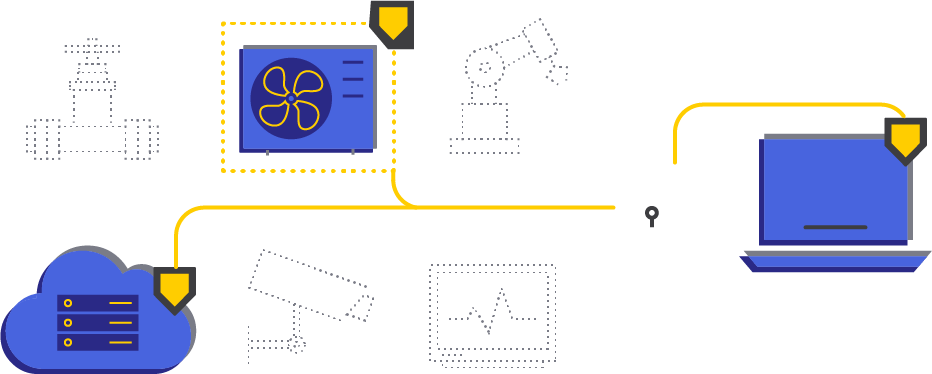
now, only authorized assets can communicate over a secure, encrypted peer-to-peer tunnel.
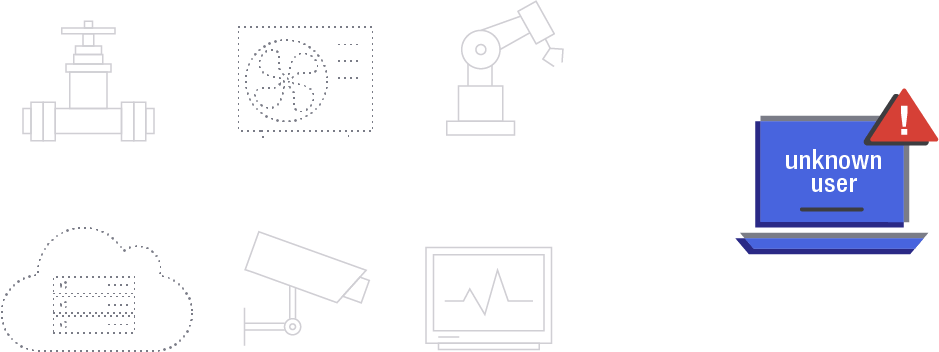
cannot see or attack Airwalled devices because they're invisible.
This site uses cookies to enhance your browsing experience.
By continuing to use our website you agree to our Privacy Policy